What is IT security?
IT security protects the integrity of information technologies like computer systems, networks, and data from attack, damage, or unauthorized access. A business trying to compete in a world of digital transformation needs to understand how to adopt information security solutions that begin with design. This is what it means to "shift security left"—to make security a part of the infrastructure and product lifecycle as early as possible. This helps security be both proactive and reactive.
Continuous security is fed by a routine system of feedback and adaptation, often handled through the use of automatic checkpoints. Automation ensures fast and effective feedback that doesn’t slow the product lifecycle down. Integrating network security in this way also means that updates and incident responses can be implemented quickly and holistically as the security landscape changes.
Why is cybersecurity important for business?
Traditionally, IT and cybersecurity was focused on fortifying, maintaining, and policing the datacenter perimeter—but today that perimeter is dissolving. The way we develop, deploy, integrate, and manage IT is dramatically changing. Public and hybrid clouds are redistributing responsibility for regulatory compliance and data security across multiple vendors. The adoption of containers at scale requires new methods of analyzing, securing, and updating the delivery of applications. Mobile apps are spread across a multitude of devices, and more and more infrastructure is moving from hardware to software. More complicated networks of devices or processes can increase the risk of security compromises, like insider threats or malware.
The traditional ways of managing security aren’t keeping up. Digital transformation demands a change in IT security services and programs—security must be continuous, integrated, and flexible in a digital world.
For some businesses, doing security right means hiring a Business Information Security Officer. BISOs are embedded in the business and involved in the product lifecycle from design to delivery and adoption. Often alongside security analysts, they report to the Chief Information Security Officer (CISO) to make sure that security initiatives and concerns are thoughtfully managed and integrated at every stage, balancing security needs with risk to the business to ensure fast delivery that functions as it should.
What is Linux security?
Security-Enhanced Linux (SELinux) is a security architecture for Linux® systems that allows administrators to have more control over who can access the information system. It was originally developed by the United States National Security Agency (NSA) as a series of patches to the Linux kernel using Linux Security Modules (LSM).
SELinux was released to the open source community in 2000, and was integrated into the upstream Linux kernel in 2003.
Manage security and compliance risk on open source Linux
What is Zero Trust IT security?
Zero Trust is an approach to designing network security architectures based on the premise that every interaction begins in an untrusted state. This contrasts with traditional architectures which may determine trustworthiness based on whether communication starts inside a firewall. More specifically, Zero Trust attempts to close gaps in security architectures that rely on implicit trust models and one-time authentication.
Zero Trust architecture has gained popularity because the global cybersecurity threat landscape has evolved, challenging long held assumptions about the inherent trustworthiness of activities inside a network. Well-organized cybercriminals can recruit insiders, and continue to find new ways past the outer shell of traditional security architectures. Sophisticated hackers and commercialized ransomware-as-a-service platforms have also become more widely available, making it easier for new kinds of financially-motivated cybercrime to occur. All of these cyberthreats have the potential to exfiltrate valuable data, disrupt business and commerce, and impact day-to-day life.
What is DevSecOps?
DevSecOps is the combination of DevOps practices and security strategies as a means for organizations to increase IT security and reduce risk to their software environments. DevSecOps can enable an organization to secure their software environments faster, at larger scale, and more comprehensively when compared to traditional IT security strategies.
What is container security?
Containers make it easy to build, package, and promote an application or service across different environments and deployment targets. But there are some challenges to container security. As more businesses adopt container technologies, security teams have new adversary models to combat and new infrastructure components to secure.
Static security policies and checklists don’t scale for containers in the enterprise. The supply chain needs more security policy services. Teams need to balance the networking and governance needs of containers. A successful organizational container security program must implement key controls throughout the build, deploy, and run phases of the container life cycle as well as in the underlying container infrastructure.
Not sure where to start? Watch this webinar series to get expert perspectives on the need and value of security throughout the entire container application stack and lifecycle.
What is cloud security?
While many people understand the benefits of cloud services, they’re equally deterred by the security threats. We get it. It’s hard to wrap your head around something that exists somewhere between amorphous resources sent through the internet and a physical server. It’s a dynamic environment where things are always changing—like security threats.
While the adoption of cloud-native technologies creates new security challenges, it also creates opportunities to enhance existing security strategies. The goals of an effective cloud-native security strategy should allow teams to achieve greater levels of software delivery while building more secure systems.
What is hybrid cloud security?
Hybrid cloud environments offer users a lot of choice and flexibility. You can keep critical or sensitive information off the public cloud while still taking advantage of cloud providers for data that doesn’t have the same kinds of risk associated with it. Here are some of the challenges of hybrid cloud security, and the tools you need to solve them.
What is API security?
You probably don’t keep your savings under your mattress. Most people keep their money in a trusted environment (the bank) and use separate methods to authorize and authenticate payments. API security is similar. You need a trusted environment with policies for authentication and authorization.
API security best practices include the use of tokens, encryption and signatures, quotas and throttling, and an API gateway. Most importantly, though, API security relies on good API management.
What is malware?
Malware, short for malicious software, is any software that acts against the interest of the user. From ransomware to adware to botnets, malware is responsible for destroying data, violating people's privacy, and causing countless hours of lost productivity. Malware—sometimes delivered via phishing scams—can affect not only the infected computer, laptop or device but potentially any other device the infected device can communicate with. Malware attacks are a severe threat, but effective IT security can reduce your organization’s vulnerabilities and exposure to cyberattacks.
What is Kubernetes security?
Kubernetes (also known as k8s or "kube") is an open source container orchestration platform that automates many of the manual processes involved in deploying, managing, and scaling containerized applications. IT security teams need to understand Kubernetes and cloud-native technologies sufficiently to establish effective preventative measures and risk management.
Kubernetes-native security provides deeper insight, faster analysis, and simpler operations, reducing the overall investment in time, effort, and personnel required to implement security.
What is CVE (Common Vulnerabilities and Exposures)?
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. CVE is also shorthand for the CVE ID number assigned to a security flaw. CVEs help IT professionals coordinate their efforts to prioritize and address these vulnerabilities to make computer networks more secure.
What is vulnerability management?
Vulnerability management is an IT security practice that involves identifying, assessing, and remediating security flaws in devices, networks, and applications, in order to reduce the risks of cyberattacks and security breaches. A vulnerability management program helps security teams automate their detection and remediation processes, including vulnerability scanning and patching.
What is Red Hat's approach to hybrid cloud security?
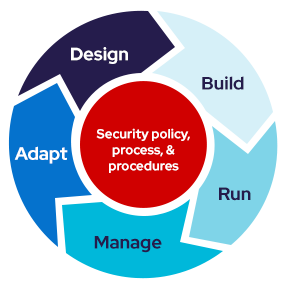
Containers and hybrid cloud technologies have made the security landscape much more complex. Security teams are increasingly finding it challenging to keep up with the changing risks, compliance requirements, tools, and architectural changes introduced by these technologies. Traditional perimeter-based network security is no longer effective on its own, and security teams must rethink their approach.
Red Hat’s layered, defense-in-depth security as code approach helps customers implement security across the entire infrastructure and application stack and life cycle.
Want to report a vulnerability? Need help now?
Connecting with a community and solving problems together is the future of security.
Red Hat and IT security
We want you to have confidence as you adopt a continuous security strategy. We do that by making open source ready for the enterprise. Our goal is to help your business remain competitive, flexible, and adaptable while maintaining IT security and regulatory compliance.
Red Hat's unique subscription model gives customers access to a dedicated team of experts who support our technology 24x7. Here are just a few of the things we can offer you as part of your open source security solutions.
Trained and certified
Are you up to date with government security standards? Let us make this process as easy as possible for you.
Know which issues are branded, and which really matter
A vulnerability may get a catchy name, fancy logo, or media attention. That doesn’t mean it poses a material risk to users. We assess issues so you can know the difference.
Collaborative and accountable
We are committed to providing tools and security data to help security measurement. We also provide raw data so customers and researchers can produce their own metrics, for their own unique situations, and hold us accountable.
What you need to know about digital transformation
Security today is informed by digital transformation. But what exactly is digital transformation? Where does the concept come from? Where is it going? What does it mean for you?
Trust Red Hat
Learn about Red Hat’s commitment to protecting customer data and privacy





